Ansible is one of my favorite tools. I use them for almost everything – system configuration, servers provisioning, serverless services provisioning and even for calling API that hasn’t its own Ansible module. You can do everything with Ansible! Moreover, you can also use Jenkins to run Ansible. I’m very glad that it’s possible and I use that possibility as often as possible. Of course, only if it makes sense. Also, I’m sure that it’s normal practice, as somebody develops an Ansible plugin for Jenkins. Anyway, one of the very, very important Ansible’s feature is ansible-vault, that allows to encrypt sensitive data and decrypt on the fly. It, of course, needs a password during the playbook run. So how can we use an ansible-vault password in Jenkins job? In a very simple way!
So what’s the problem with an ansible-vault password in Jenkins?
Look, I assume right now, that you already know what ansible-vault is and you know how to use that fantastic feature. If you’re not familiar with it, please visit Ansible Documentation. Anyway, if you’re here, it means that you probably are looking for a solution on how to use an ansible-vault password in Jenkins. Because you know, in theory, it’s very simple. You have a playbook, you have (for simpler example) a vault and you call it in your playbook. One of the simplest examples of using ansible-vault can be the following command:
|
1 |
ansible-playbook -i hosts.ini playbook.yml --vault-id @prompt |
As a result, it will ask you about the password for decrypting ansible-vault. You will provide that and then the playbook will be executed. But you cannot (or shouldn’t) do something like that in Jenkins.
Jenkins jobs should be as automated as possible (with some, specific exceptions). Prompting for anything is not a good idea. Passing sensitive data as a string/password parameter is also not a good idea. Sometimes jobs should be possible to start by more persons (e.g. Developers) which shouldn’t know the vault password. Moreover – they shouldn’t be able to decrypt vault file and see what it contains! So you need a way in which you are able to configure your job and use an ansible-vault password in Jenkins in an as simple and secure way as possible. And do you what can help you? Jenkins credentials and the fact, that you can use a file to provide an ansible-vault password!
Use the file as the way of providing a password!
Ok, the first and the most basic information you need to know is:
“When all data is encrypted using a single password the –ask-vault-pass or –vault-password-file cli options should be used”.
Yup, the “all data is encrypted using a single password” is the key in this article. I described only the most basic example, where you don’t have multiple vaults with different passwords, as it’s a more complicated situation that appears mostly in more complex playbooks. I just wanted to show you the basic concept.
So, we know that we can use a file with a password. So the real example could be:
|
1 |
ansible-playbook -i hosts.ini --vault-password-file /path/to/my/vault-password-file playbook.yml |
But how to use that way to provide an ansible-vault password in Jenkins? Like everything – in a very simple way!
First, use Jenkins credentials!
If you want to store your ansible-vault password in a secure way and be sure that you can update the password whenever you want without a negative impact on your jobs, you need to use Jenkins credentials. If you don’t know how to use credentials, please see another article in this blog. A short tutorial:
First of all, create a text file on your own computer and put a password inside – WITHOUT any additional blank spaces.
Then go to Jenkins -> Credentials and create a new credential (if you don’t know how, please visit my post about creating credentials in Jenkins). Choose the “Secret file”. Now, you need to add any ID and description (please remember to use a descriptive and meaningful ID!) for your new credential. Then, when you click on the “Choose file”, you will be able to choose the file with your password. As you can see on the screenshot below, after choosing, you will see the name of your file right next to the button (in my case it was “valut_file”).

Now you can save the credential and see if it’s visible on the credentials list.

Second, choose your favorite way of running playbooks in Jenkins!
Yeah, you already have a properly encrypted password, so you can use your favorite way of running playbooks and just pass the ansible-vault password in Jenkins job. Basically, you probably configure your job in one of two ways:
- by using Ansible plugin
- by using an Execute shell step
Ansible plugin way
If you use the Ansible plugin, you’re in a very simple and comfortable situation. This plugin has its own field for an ansible-vault password – please see the image below.

You just need to choose the valid credential and that’s all – plugin will do the magic for you. Of course, it can be configured also with Jenkins DSL:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 |
steps { ansiblePlaybookBuilder { playbook("playbook.yml") inventory { inventoryPath { path("hosts.ini") } } additionalParameters("-b") ansibleName("ansible-main") becomeUser("false") colorizedOutput(true) credentialsId("") disableHostKeyChecking(false) forks(5) hostKeyChecking(true) limit("") skippedTags("") startAtTask("") sudo(false) sudoUser("") tags("\") unbufferedOutput(true) vaultCredentialsId("my_vault_file") } } |
Execute shell way
If you prefer this way, you need to add an additional section to your job – “Use secret text(s) or file(s)” in the “Build Environment” section of the job, like here:

You can, of course, read more about adding credentials to your job in another article. In this way, you can bind credentials to your job, and with the variable that you specify (in this scenario variable is named “my_vault_file”, just like credential ID) and then you will be able to use an ansible-vault password in Jenkins shell job. If you have that, then you can just create a Shell execute step:
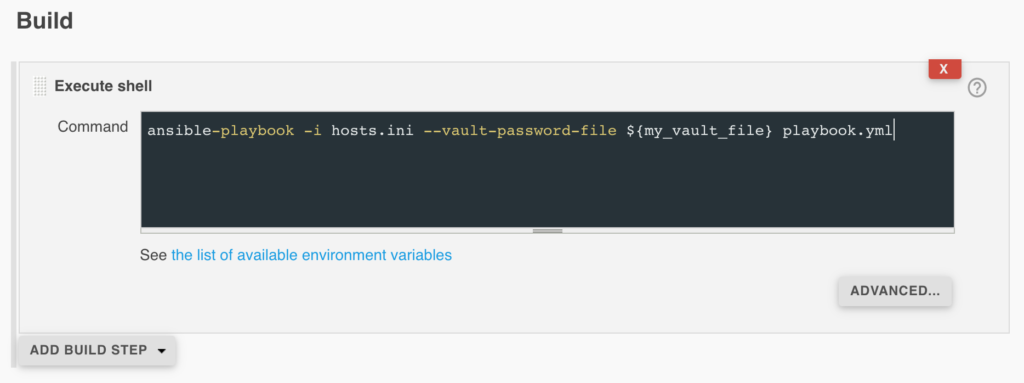
And that’s all. You can use this article to build your own solution and/or adjust that to your needs. 🙂
Thanks Emil! Just what I needed. The documentation on this is pretty much useless.
I’m glad you found that useful. 😀
First, thanks for your useful post! I have been trying to implement the above in my jenkins/ansible setup, it is supposed to open a LUKS encrypted paritition, but in both methods, I was unsuccessful:
1. In the “ansible plugin” method:
cryptsetup throws password not correct error. When I check during the run, the ansible encrypted key file is not decrypted (don’t know why)
2. In the “shell” method:
Either it throws the error “The vault password file /blah/blah/workspace/Backup/vault-key was not found” using secret file as an option and passing the credentials variable –vault-password-file to ansible. Same error when I use secret text instead of secret file.
NOTE: I’m using a jenkins node to run ansible, as it is taking backups from infra and i did not want to mess it with jenkins setup.